
Tailored QR Code Templates for Phishing Scams
Sundar Balasubramanian, India and SAARC MD, Check Point Software Technologies

Introduction
QR Code phishing—or Quishing—has continued to be a hot topic in email security.
Since August, we’ve seen a massive increase in QR phishing, one that continues as we move further into the year. QR phishing scams have unfortunately been on the rise in India. Recent reports state that the number of UPI frauds had increased from 15,000 cases in 2022 to a staggering 30,000 cases in 2023.
The proliferation of QR phishing scams in India can be attributed to factors like the widespread use of mobile phones, the increasing adoption of digital payment systems, and a lack of awareness regarding cybersecurity best practices. QR phishing cases registered in Bengaluru alone between 2017 and May 31, 2023, highlight the significant impact of these scams on individuals and businesses, leading to financial losses and hindering digitalization efforts in India.
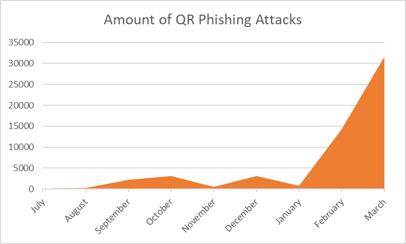
Hackers are constantly finding new ways to deploy QR codes in phishing campaigns. In recent weeks, we’ve covered the usage of Conditional QR Code Routing Attacks.
Now, Harmony Email Researchers have found a new QR campaign, where the hackers are using custom templates specific to each organization, making every attack unique to the company and individual. Over the last 14 days, we’ve found over 2,000 of these emails spread to over 1,100 customers.
Email Example
This attack tries to pose as an authentication update.
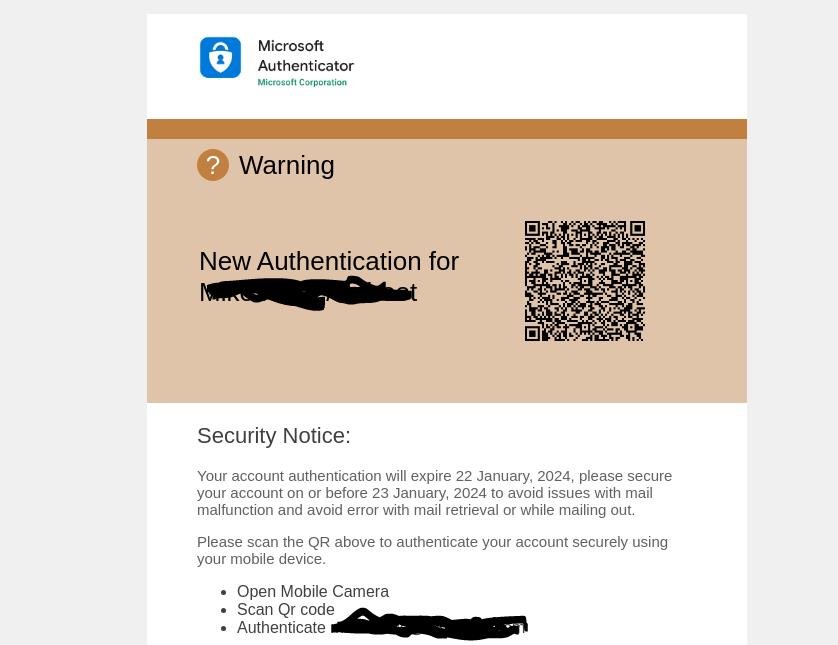
It notes that account authentication will quickly expire. To avoid mail disruption, you need to re-authenticate the account.
We’ve blacked out and cut off a few pieces of information for safety purposes. At the top, which we cut off, the legitimate company logo is present. This changes dynamically depending on the company targeted. This makes the phishing attack seem more legitimate and personalized.
We’ve also blacked out the part where the hackers insert the name and user name of the victim. Again, this is populated dynamically.
Here’s another example:
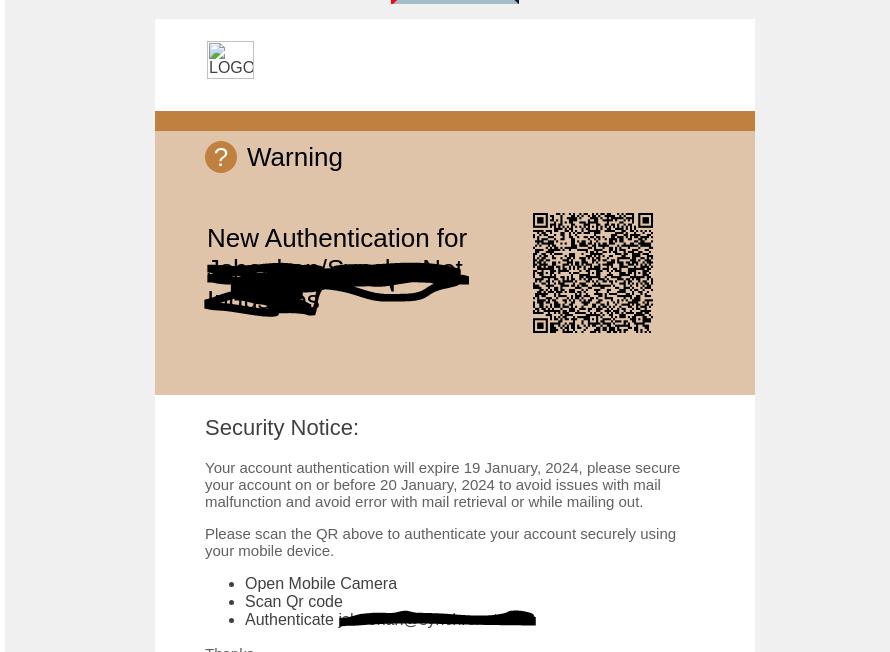
The formula is the same—add company logo, add victim name, and implore them to update their authentication before incurring issues with their email.
Were the user to scan the QR code, they would be led to a credential harvesting site.
Techniques
This is a particularly tricky and clever attack. It’s incredibly personalized and targeted, by providing the legitimate company logo and using the correct name and user name. By changing dynamically depending on the target, this attack is scalable, as well.
It plays on urgency. By suggesting that email access will be altered, users might be inclined to act quickly.
The usage of the QR code also conveys a layer of trust. End-users are accustomed to using QR codes, although less so in a business context than as a consumer. Still, it’s a technology that’s familiar.
And, since you have to scan the QR code on your phone, it also opens the door up for a compromise on that device.
In short, this is a crafty attack that has the potential to cause serious damage.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
â— Implement security that automatically decodes QR codes embedded in emails and analyzed the URLs for malicious content
â— Utilize security that rewrites the embedded QR code in the email body and replaces it with a safe, re-written link
â— Implement security that utilizes advanced AI to look at multiple indicators of phishing
â— As always, if it is urgent or feels out of the ordinary, do not scan the QR Code
CIO Viewpoint
Upcoming Technological Advancements in Payments...
By Pinak Chakraborty, CIO of Airtel Payments Bank
Shaping the Future of AI: Talent, Innovation,...
By Yann LeCun, Chief AI Scientist at Meta
Future of Smart Manufacturing: Integrating Tech...
By Mohammed Kaishulla, Chief information officer, EPACK Durable
CXO Insights
Tailored QR Code Templates for Phishing Scams
By Sundar Balasubramanian, India and SAARC MD, Check Point Software Technologies
Emerging Trends, Challenges & Future Prospects...
By Sujoy Brahmachari, CIO & CISO, Rosmerta Technologies
Exploring Data-First Security and Automation in...





.jpg)
.jpg)
.jpg)








